Table of Contents
BTreeMap
std::collections::BTreeMap
BTreeMap is a type from Rust’s …
Learning new things!
std::collections::BTreeMapBTreeMap is a type from Rust’s …
This blog is the learning note for Brainfuck VM
Using the following example to go through GKR protocol
this blogs follows the example in Spartan 预备知识:GKR with ZK Argument
zero knowledge version of GKR, Hyrax approach.
Using an example of 3 variants multilinear polynomial to explain the design idea of sum-check protocol.
A 3 variants multilinear polynomial can be generally represented as
$$g(X,Y,Z)=a_0+a_xX+a_yY+a_zZ+a_{xy}XY+a_{xz}XZ+a_{yz}YZ+a_{xyz}XYZ$$
In the final round of sumcheck protocol, assuming the verifier gets a one degree polynomial
$$h(z)=g(r_1,r_2,\ldots,z )=\alpha_n z …
Following the definition from Justin Thaler
Let \(\mathbb{F}\) be any finite field, and let \( f : \{0,1\}^v \rightarrow \mathbb{F} \) be any function mapping the \( v \)-dimensional Boolean hypercube to \(\mathbb{F}\). A \( v \)-variate polynomial \( g \) over \(\mathbb{F}\) is said to be an …
These will be a series post about FFT and the math structure behind it. My goal are:
However, …
Take example circuit in figure 1, following the Arithmetization described in post, a step by step description of GKR arithmetication of a concrete example.

\(q’\in \{0,1\}^{b_N}\): The index of one of the \(N\) identical copies of the base circuit \(C_0\) within \(C\).…
To understand the attack on Nova, I figure out I need to understand the role of the hash function and the validation check of hash function in Nova, from the first paper where the “cycle of curves” is not introduced, the circuit is illustrated as
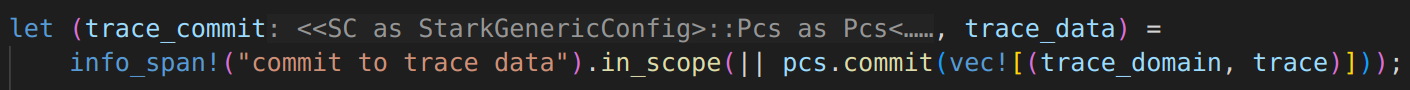
to …