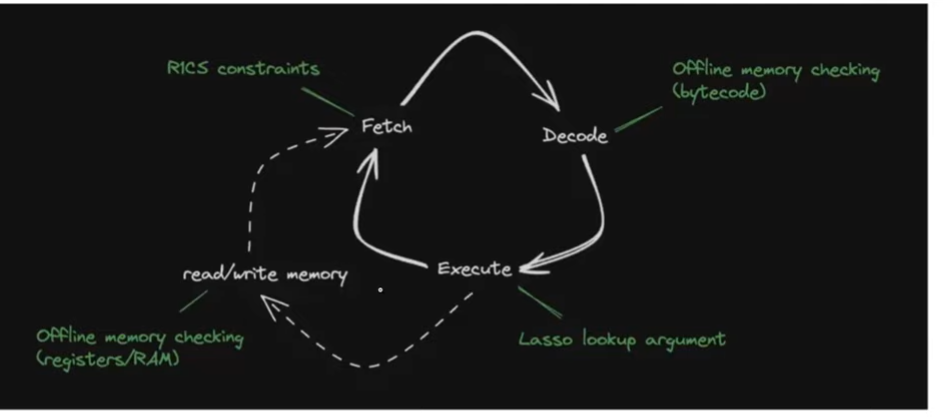
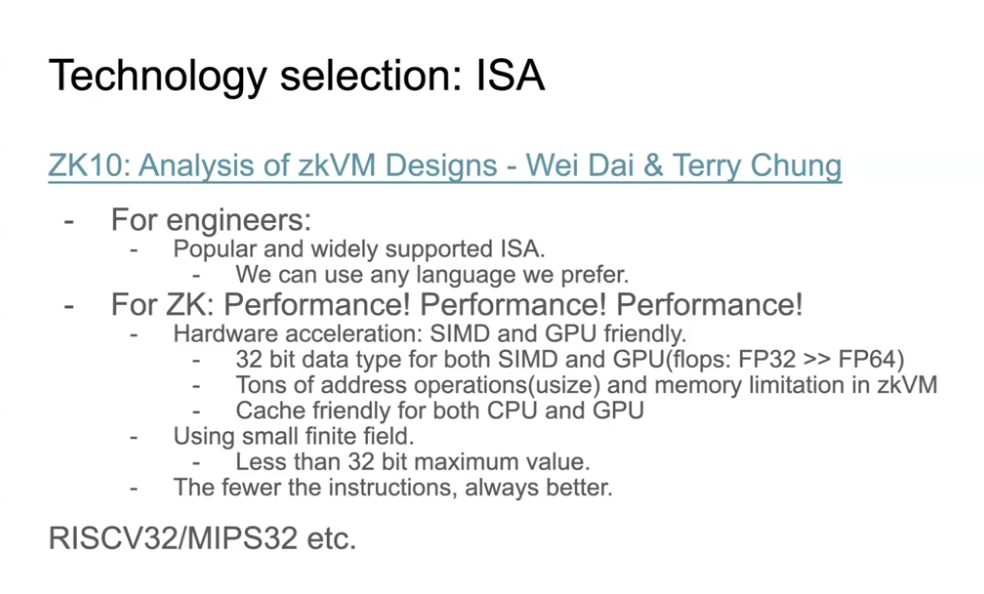
Table of Contents
- What is Runtime?
- Runtime Environment
- Runtime Systems
- Runtime Errors
- Runtime Libraries
- Examples in Context
- What is a Processor?
- What is a CPU?
- Key Difference Between Processor and CPU
- Analogy
What is Runtime?
Runtime refers to the period when a program is actively running or executing on a …